I'm a proud parent raising kids in an Internet-connected age. And I've spoken with many parents also trying to do the same. And while there is so much good stuff out there on the Internet, there is also so much bad stuff... And we don't want them accidentally stumbling on it. While there is no technology silver bullet to filter out all the bad while leaving the good, there are a few good free choices that can help protect against accidentally stumbling on bad stuff.
Google, YouTube, and Microsoft's Bing all provide a method to enforce that their "safe" modes are enabled by doing some clever tricks with DNS. Thanks to OpenDNS for documenting this. I wanted to set this up for myself and some clients and friends so that our home routers would enforce this. There are some other ways to set this up that involve multiple files; the way below only involves configuring dnsmasq (the default DNS server on OpenWRT).
Google, YouTube, and Bing all provide this service the same way: force their main domain name(s) to resolve to a particular IP address. They each have some dedicated IPs setup for these alternative servers which enforce safe search modes. Normally, all you should need to do is setup a CNAME record. But dnsmasq won't resolve locally-defined CNAMEs for you, it assumes you already have a local host record for it. So you'll also have to define a host-record explicitly defining the resolution of the CNAME. This is fine for today, but if Google, YouTube, or Bing ever change the IPs, this setup will break... So far, I've been using this for a year or so with no changes required.
Here's the config to add to your /etc/dnsmasq.conf file.
# force google safesearch
host-record=forcesafesearch.google.com,216.239.38.120
cname=www.google.com,forcesafesearch.google.com
# force bing family filter
host-record=strict.bing.com,204.79.197.220
cname=www.bing.com,strict.bing.com
# force youtube restricted mode
host-record=restrictmoderate.youtube.com,216.239.38.119
cname=www.youtube.com,restrictmoderate.youtube.com
cname=m.youtube.com,restrictmoderate.youtube.com
cname=youtubei.googleapis.com,restrictmoderate.youtube.com
cname=youtube.googleapis.com,restrictmoderate.youtube.com
cname=www.youtube-nocookie.com,restrictmoderate.youtube.com
Once you've got that set, you'll have to restart dnsmasq:
/etc/init.d/dnsmasq stop
Wait just a moment to make sure all of its sockets are released...
/etc/init.d/dnsmasq start
Voila! SafeSearch enabled and enforced across ALL devices!
Testing
To verify, I did a ping before I made the change:
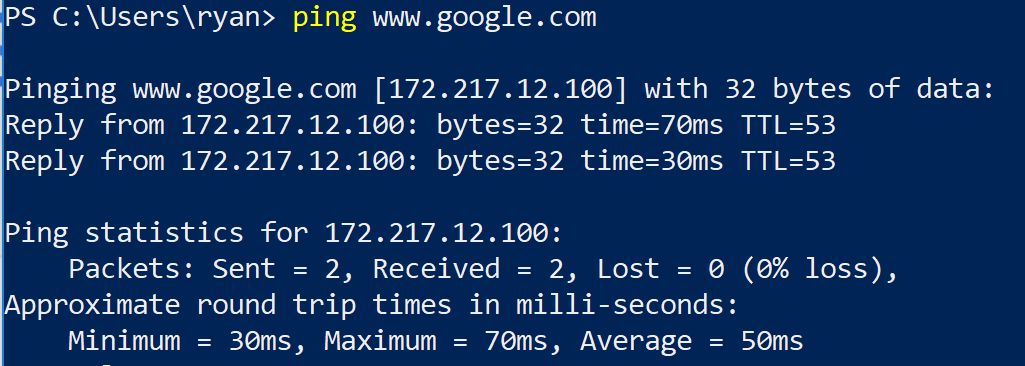
And after I made the change:
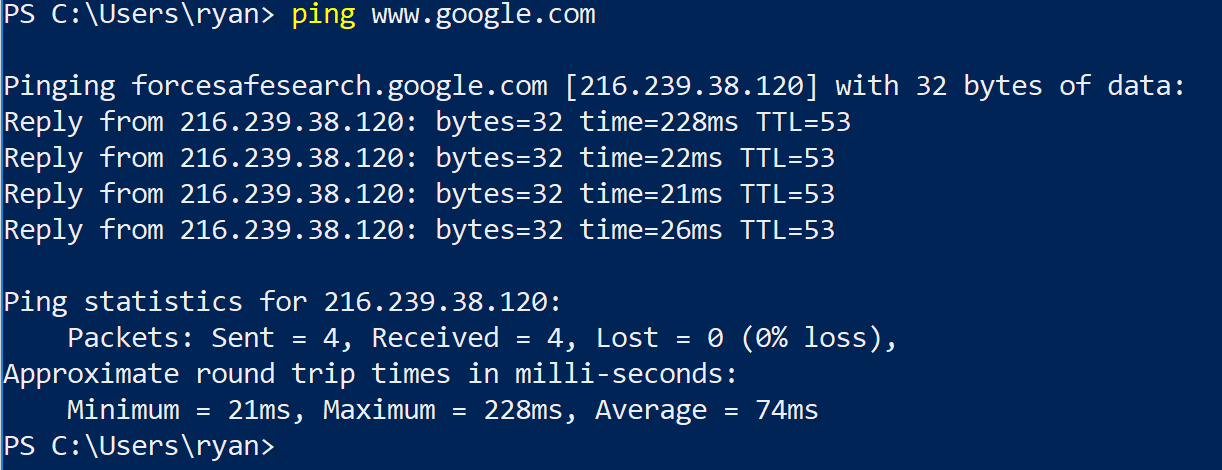
Note that the reverse name shows that we are using the forcesafesearch.google.com server.
Testing Google SafeSearch
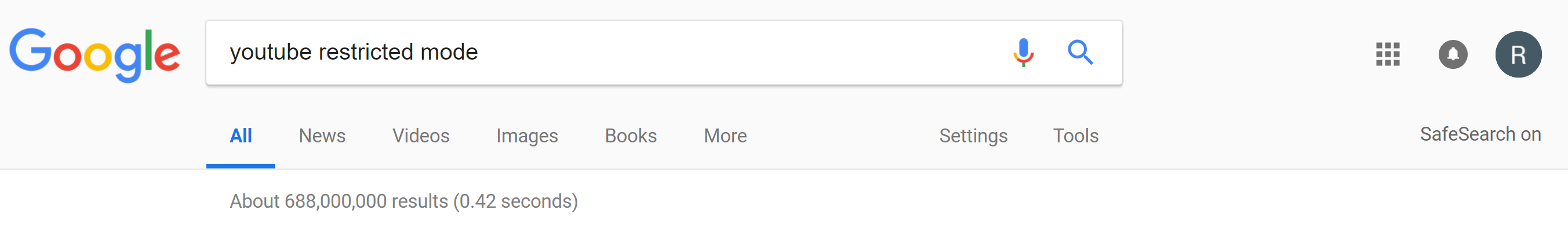
You can confirm that Google's SafeSearch is on by testing a Google search. I searched for "youtube restricted mode". On the right side of the navbar at the top of the page, you'll see the text "SafeSearch on":
Normally, you can disable SafeSearch under the settings menu:
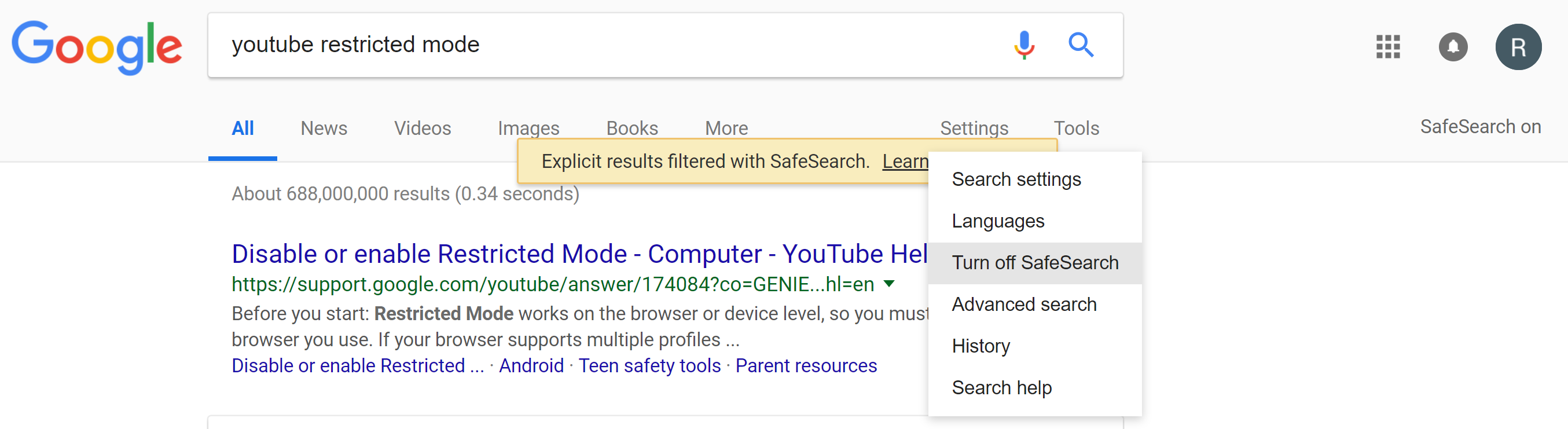
Try clicking on "Turn off SafeSearch". The page should refresh, but if the "SafeSearch on" text doesn't go away, then it is forced on.
YouTube Restricted Mode
For more information about YouTube's restricted mode, check out this page that discusses YouTube's different restricted modes and this page that discusses restricted mode in general
For example, in restricted moderate mode, comments are disabled on Youtube:
Locking This Setup Down
If you really want to be sure that no one can circumvent these settings, you should block and DNS requests that don't pass through your DNS. Practically this can be achieved by blocking all TCP and UDP requests to port 53 on the iptables FORWARD chain. Here's how I implemented it in /etc/config/firewall:
config rule
option name Block-alternative-TCP-DNS
option src lan
option proto tcp
option family ipv4
option dest wan
option dest_port 53
option target REJECT
config rule
option name Block-alternative-DNS
option src lan
option proto udp
option family ipv4
option dest wan
option dest_port 53
option target REJECT
Then bounce the firewall:
/etc/init.d/firewall stop
/etc/init.d/firewall start
Conclusion
This is a free filtering solution that's pretty easy to setup with some tech skills and OpenWRT. Just remember that no filtering solution is fool-proof. Don't trust filtering like this to replace talking with your kids about the good and the bad of the Internet. I use filtering to prevent accidents for the whole family, but we supplement it by having rules about how our kids use the Internet and by constantly talking to them about the Internet and the good and bad stuff out there.